(how I feel when talking about this topic)
(how I feel when talking about this topic)
How information is obtained and what is classified as a “threat” varies vastly between organizations. After consuming books, blogs, articles, youtube, and performing threat intelligence, I can say no one seems to do it the same. This is due to every organization having different motivations and abilities. In this blog post, I will define what Cyber threat intel is and some of the standard terms and guidelines I’ve learned running an intel program.
What is Cyber Threat Intelligence(CTI)? I asked that question years ago when I got put in charge of an intel program for a FinTech company. The simple answer is that CTI is information gathered, analyzed, and disseminated to help organizations understand and defend against potential cyber threats. It includes details about known and emerging threats, as well as the context and insights needed to prioritize and respond to them. It enables people and systems to make informed decisions on how best to defend their brands, their customers, and themselves.
The intelligence provided must meet several criteria, regardless of the audience—the first being accuracy. The intelligence provided must be reliable and detailed. Reporting without sufficient information can lead to false flags and wasted efforts. Second, the information must be relevant to your organization. Reporting on a new vulnerability may require you to verify that your organization is using that software. Before writing up that report on the latest hot threat actor, make sure they are targeting your industry. Lastly, intelligence needs to be timely. This requires CTI analysts to be on the lookout for the latest techniques, breaches, and vulnerabilities. Being able to report the day the news drops can be overwhelmingly valuable for your organization. Saving vast amounts of money and effort. Making sure your CTI is accurate, relevant, and timely is a challenging feat but a must for a good CTI program.
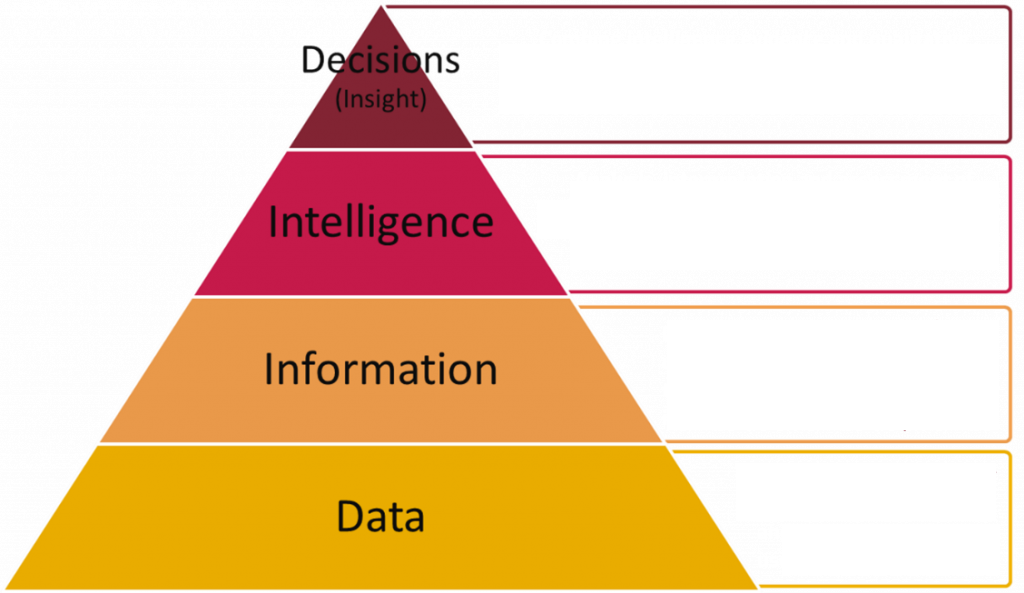
Now let’s define the terms data, information, and intelligence. Data consists of discrete facts and statistics gathered as the basis for further analysis. Information consists of multiple data points that are combined to answer specific questions. Intelligence is the output of an analysis of data and information that uncovers patterns and provides vital information for your organization’s decision-making.
Intelligence is not given; it’s made. Suppose I give you a threat report on the latest TTPs used by Green MirrorCat that would be considered data or information. Intelligence must be modified with your organization in mind. Once an analyst consumes this information and tailors it to your organization, it becomes intelligence.
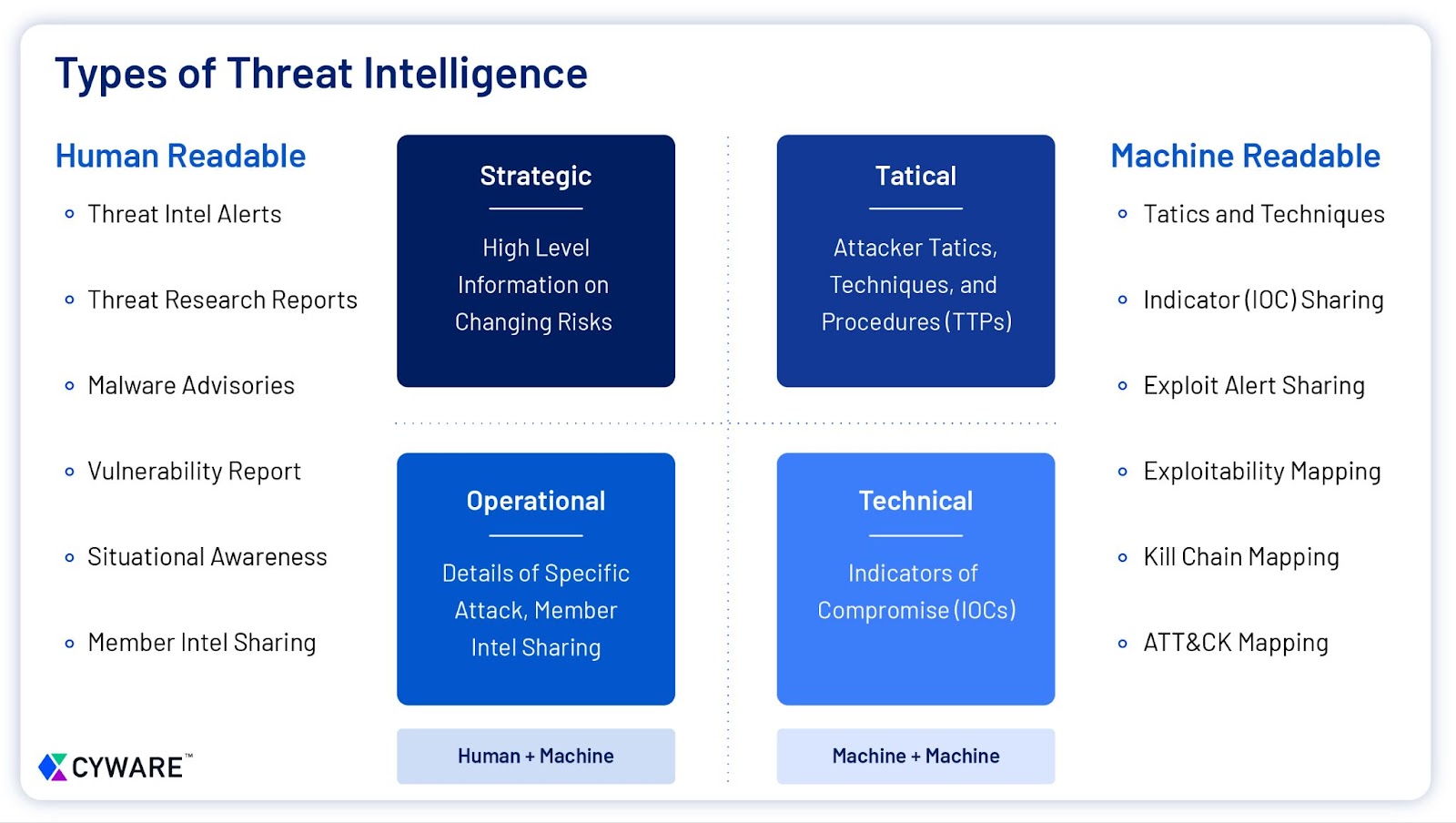
Intelligence can fall into several categories depending on what you’re reading and who you’re talking to. The four types of intel that I view are Tactical, Strategic, Operational, and Technical.
Strategic Intelligence is related to the risk of the organization. It is usually made from government policies, news sources, Industry reporting, or social media. Strategic intel is provided to upper-level decision-makers and usually less technical leaders. Some end-product examples would be.
- Intel Reports
- Threat Briefings
- Executive Summaries
Operational Intelligences focuses on how and when a threat actor will attack an organization. It is usually both technical and strategic in providing information on the intent, capabilities, and timing of impending attacks. This type of intelligence is usually the hardest to create. Sources that would generate this type of intelligence are from:
- Forums
- Chats
- Message board
- Darkweb
- Agencies…
Tactical intelligence relates directly to threat actors’ tactics, techniques, and procedures (TTPs) to achieve their objectives. It is usually provided to the teams defending an organization to build detections and preventions. It can be made from malware analysis, intel reports, vendor reports, or general news on breaches. Examples of tactical intelligence are:
- Threat reports
- campaign activity
- infection vector
- The infrastructure used by an attacker
- TTP of the Threat actors targeting your industry
Technical Intelligence provides indicators of compromise(IoCs). It relies on these atomic indicators, whereas tactical intelligence depends on TTPs. This type of intelligence should be automated as much as possible to create detection and prevention to defend the organization. An “Aging Out” strategy should also be looked into for older IoCs. Technical intel is usually consumed via made with threat feeds or badly written reports. Examples of Technical Intelligence are:
- IPs
- Hashs
- Domains
- Emails:
Intelligence varies vastly between organizations and the departments in them. People have different definitions and understandings of what the CTI does. It’s essential to lay down some definitions at the beginning of talking to people within your organization about CTI. Hopefully, this helped you understand some of the basics of CTI and gave you ideas to pivot on to learn for yourself.
Resources:
There are a large amount of resources to really dive into what CTI is. I usually try to stay away from vendor blogs, but these few have some great write ups.
What is Cyber Threat Intelligence by Agari